Some thoughts on Confide
Secrecy in the White House has always been a hot topic. However, a recent Washington Post article highlights use of the Confide app:
Staffers, meanwhile, are so fearful of being accused of talking to the media that some have resorted to a secret chat app — Confide — that erases messages as soon as they’re read.
Some have expressed concern about how this could be a breach of the Presidential Records Act, or how the use of Confide means that national secrets could end up flowing through Confide’s servers and/or the public Internet. I’m not here to make claims about legality though (although I do have strong opinions on this, and many other things). The following attempts to answer a few simple questions about Confide that I hope helps you draw your own conclusions.
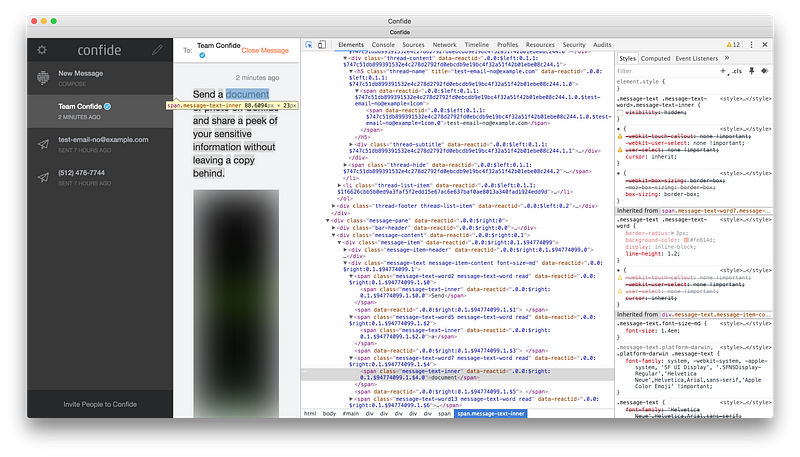
So, what’s up with Confide?
I go into more technical detail below, but here’s the quick version:
- Confide is decently confidential and secure for a certain threat model: casual intrusion, over-the-shoulder snooping, and other things of that level. It’s a definite upgrade from unencrypted email.
- Of course, all bets are off if an attacker has access to your machine. It’s trivial to disable “screenshot protection”, secretly record messages before they are deleted, and find a conversant’s private key.
- An attacker with network access will be able to see some metadata, but might not be able to access conversation contents.
- Finally, I don’t have enough knowledge to say what happens to messages once they hit Confide’s servers. There are no guarantees of deletion.
So, to sum up: better than Snapchat. Good for sharing personal secrets, or maybe even sharing some sensitive material in the corporate world. Certainly not ideal for government secrets. But that should have been obvious.
Why do this?
Well, I was bored. But also—Confide is a for-profit company which makes claims about security, but their methods and application source code have not been audited. On the other hand, the Signal protocol which underpins WhatsApp, Signal, and a few other applications, has undergone a formal audit (PDF). This doesn’t necessarily mean that Confide is good or bad. I’m not a cryptographer and I’m not doing protocol analysis. It’s just that we know basically nothing about the app at this point.
Looking at Confide’s claims
I’ve highlighted a few phrases from the Confide home page that I’ll examine.
“Protecting your messages from screenshot attempts”
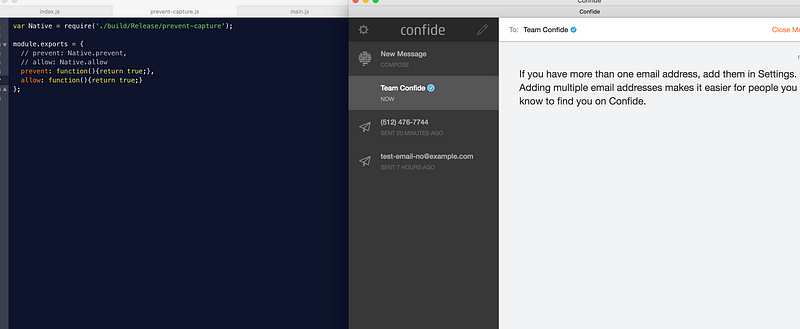
This is done through a piece of native “helper” code which interfaces with the macOS graphics system to draw a grey rectangle on top of the window when a screenshot event is detected. However, the helper code interfaces with JS through a JS module. Judicious editing of the module’s exported functions completely disables this protection. You could also just take a picture of the actual screen with your camera.
“Messages disappear forever”
The fancy “redacted” effect is all done in CSS / JavaScript. Data remains in the app page’s DOM tree as HTML elements. This isn’t bad — it’s good UX and effective against “shoulder surfing” and so on.
Like I mentioned earlier, all bets are off if you have machine access. Since the UI is a web page, a few lines of JavaScript are all that’s needed to preserve messages as they pass through the app after decryption. This is made doubly easy by the fact that the app doesn’t check the integrity of its own files, meaning edits could go unnoticed.
“Military-grade end-to-end encryption” and “Transport Layer Security”
Military grade: What does this even mean? It sounds good in marketing material, so I guess I’ll give them a pass on this.
End to end: Messages are encrypted using the node.js “crypto” library’s functions, which is good—they’re not rolling their own software. The nitty gritty: messages are represented as a JS Object, turned into JSON and base64 encoded, encrypted with a private key with the aes-256-cbc cipher and a 32 bit initialization vector.
Looks like they’re doing some sort of standard key exchange based on ECDH, with ephemeral keys. Beyond that, I can’t tell much.
Transport security: The app does indeed use TLSv1.2, a secure and accepted standard for encrypting data in transit. Communication with the server happens over HTTPS and SSL WebSockets with certificate pinning. To get specific, the cipher suite is TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256. This is all reasonable.
Now, what if you man-in-the-middle yourself? (Or get man-in-the-middled by an adversary, or White House IT?) Well, without the private key, you can’t look at the goods—but you can see some metadata from the WebSocket, including who a new message is to/from and whether the user is using the app at that moment. There does seem to be some basic MITM detection based on comparing fingerprints of the WebSocket server with a hardcoded hash, but it’s not quite HSTS / certificate pinning.
Other stuff: API, etc
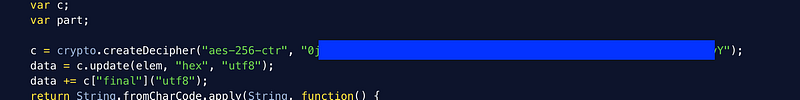
There’s a big cipher password just hanging around in the source. I don’t know what it’s for, but it doesn’t really inspire confidence. Probably innocuous though.
The application’s API seems pretty simple and looks to be based on JSON through WebSockets, with a HTTPS GET/POST based fallback (or alternate). Key exchange, message-getting, notifications, and all app communication happen through this API. There is also some sort of “access token” tied to each session, which renews. Keys seem to be ephemeral and look to be tied to this access token. Tokens are refreshed on request from the server and at the start of each session.
Note on analysis
Confide is closed source and I have no access to its source code. Luckily, the desktop client is written using the Electron stack with HTML, CSS, and JavaScript/React. In other words, it’s a really fancy web page wrapped in a stripped down browser. Unlike compiled programs, web pages are pretty hard to hide or scramble beyond a certain point. I won’t post any code here for copyright reasons, but it’s safe to say that if you know your way around a macOS app bundle and the Electron archiving format, you will *quickly* find what you’re looking for. That’s that.
The rest of my information has been gleaned from monitoring network traffic off my computer. To get at some of the encrypted traffic, I used the wonderful Charles debugging proxy to man-in-the-middle myself.
So, where does this leave us?
Maybe their marketing is overreaching a bit. Confide is good for hiding stuff from your boss or keeping a certain type of low value secret hush-hush. However, we don’t have information on their full client or server implementation (not open source), and since all data is going into Amazon’s (US-East-1), we have no guarantees on the confidentiality or integrity of information passing through the app.
Confide is a cool app with good UX. The engineers were obviously competent, they didn’t roll their own crypto, and they have a few weaknesses.
I don’t think it’s good enough for sharing information in the White House, though.